Do you want to know more about how The Cloud Collective can help protect your organisation from threats?
Insights from the field… IoT & OT
I do find myself laughing and in a moment of self-reflection pondering how I ended up in this state when I am getting annoyed with having to manually turn on the lights when the automated schedule for “all things IoT” in my house have failed (or glitched). It is true, as I am sure with many other individuals, and businesses I have been become very comfortable and to a certain degree reliant on “smart” technology.
I do confess that I have on occasion had to put my curios (ok yes… slightly paranoid) nature to rest by running a packet capture of network traffic leaving my network – just to make sure nothing obviously suspicious was occurring. As I often say (to anyone that will listen) use the right tool for the job. When we consider IoT (Internet of Things) and OT (Operational Technology) this is even more necessitated as we are often dealing with proprietary protocols and devices.
The threat landscape is complex (you can read articles about the plethora of organised groups); it is also opportunistic and bad actors will seek out and target organisations, individuals and elements that will yield maximum value, or further their cause (which includes as many motivating factors as there are groups!).
An evolving threat landscape
The threat landscape is continually evolving, this is simply a given.
As we work with organisations across various sectors we are starting to see (to a certain degree) a greater level of visibility, collaboration and a push towards common goals coming from Enterprise IT and IoT/OT groups who have either never (or rarely) been connected or reliant on each other. I believe this momentum may be driven by a several factors but summarise some as follows:
- The greater demand for inter-connectivity (Cloud)
- The advancement of tools and technology
- The “new normal” as we continue to push through COVID
Greater Demand
A study from the MPI Group, calls out the following:
- The greater demand for inter-connectivity (Cloud)
- The advancement of tools and technology
- The “new normal” as we continue to push through COVID
These are not metrics that should be ignored from a “Security Guys” perspective.
Tools and Technology
Recently awarded the Advanced Specialisation for Threat Protection, has allowed us to further bolster our capability. Certifying, testing and, working with incubation customers to onboard and evaluate Microsoft’s recent acquisition of CyberX has bolstered this front dramatically (as it aligns with our vision – ‘Effective Cybersecurity can be difficult. Complexity is often a detractor; consistency is key’).
The “new normal”
COVID has been challenging for all, manufacturers that do manage to survive will have had their strategy slate wiped clean. Gartner does an excellent job of outlining the various phases that businesses will likely go through. I would say that “cyber security” likely lives within the renew phase – but must be included as a non-negotiable.
The IoT/OT Security Challenge – do not assume you are safe. It is not if, it is when.
The effects of security breaches are staggering…
We have seen how ransomware can shut down operations. Thinking about the LockerGoga attack on Norsk Hydro, that caused $70 million in damages due to downtime. Think about NotPetya, that is now estimated to have caused $3 billion in financial losses.
Did you know?
- 64% of industrial sites are still using plaintext passwords
- 71% of sites are running older versions of Windows that no longer receive security patches
- 22% of sites exhibit indicators of threats such as scan traffic, malicious DNS queries, abnormal HTTP headers, and malware such as EternalBlue
The IoT/OT Security Approach
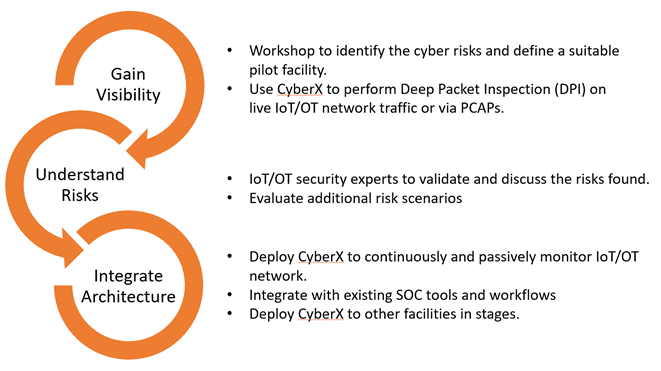
In lessons learnt “from the field” (this will continue as we work with incubation customers) several themes emerge consistently:
- Define your success early on and document what success looks like
- Continually track progress and feedback to your senior stakeholders, both on the IT and OT sides, on progress
- It is not easy to commit to deploying technology into highly critical systems (use the right tools and plan meticulously, then validate)
- Break down milestones into smaller, manageable tasks
We understand that it is not easy to commit to deploying technology into highly critical systems. The methodology defined and refined by the CyberX has proven to be invaluable. Our methodology based on this framework is designed to break down milestones into smaller, manageable tasks. Each task is designed to provide assurance that the approach does not cause interruption to production.
Cyber One – IoT/OT Module
As we continue to build on our very successful managed security platform, namely Cyber One we could not resist creating an IoT/OT module to help customers streamline security service delivery and incident management across their entire digital.
The goals are clear: Protect all IoT/OT devices and get comprehensive visibility into risk with Azure Defender for IoT. Utilize agentless network monitoring for asset discovery, vulnerability management, and continuous threat detection across all IoT/OT devices, whether they are unmanaged devices or managed devices provisioned via Azure IoT Hub. Centralize IT/OT security via integration with Azure Sentinel and Cyber One. Deploy in either on-premises or Azure-connected environments.
The IoT/OT module is designed to surface security event information related to IoT and OT workloads. The roll-up of information strategy is adopted to leverage the ability of data visualisation to enable quick decision making and confirm or re-enforce the need for further action quickly and accurately through the use of supporting information from the source as well as supplemental information (baselining as an example).
The IoT/OT module is a purpose built and comprehensive module that has coverage across the following elements:
- Asset discovery
- Vulnerability management
- Threat detection
Final thoughts (for now)
Gartner says that all functions (IT, OT, and what they call cyber-physical systems, security functions) should merge into a single organisation. It does not make sense, for example, to have a separate SOC for OT security. It does not make sense to have a different organisation be accountable in the end. It is about the security of your enterprise, the safety of your information, the safety of your people, and the safety of your assets are all part of the security organisation’s responsibility.
To get the trio on your side and start closing the gap between your organisation’s risk and capability, contact the Cloud Collective. To speak directly with a security specialist from Quorum, call (02) 8966 1400.

